
15 Dec Microsoft Azure Sentinel
Azure Sentinel is a cloud-native Security Information and Event Management (SIEM) system, which empowers security professionals to face security challenges and threats that stem from your cloud as well as on premise sources.
Azure Sentinel empowers Security Operations teams giving them an overview of the many possible threats enabling them to eliminate distractions. This means detecting and stopping threats and anomalies before they harm your data and networks.
One of its prime differentiators from traditional SIEM solutions is that tool easily connects with all your different enterprise resources using it flexible connectors and simplifies the event logging and detection process. This means analyzing huge volumes of security logs across the enterprise easily with Azure Sentinel. It lets organizations analyze security data from different sources, which include system logs, microservices and application logs, on-premise and IaaS servers and custom connectors.
Microsoft Azure Sentinel has built-in AI for Analytics and it helps to detect threats faster. Its comprehensiveness lets enterprises easily connect with custom data sources allowing to run analysis on those logs. Azure Sentinel lets you collect your data from custom sources with the support for open standard formats like CEF and Syslog.
What is SIEM?
SIEM (Security Information and Event Management) is an advanced approach to security management which merges SIM (security information management) and SEM (security event management) into one security management system.
SIEM systems have a set of best practices. It detects threats by aggregating activity logs from different sources and quickly identifying deviations from the norm to take appropriate actions.
Once a potential threat is detected, the SIEM system:
- Logs in all additional information
- Creates an instant alert
- Instructs related security controls to stop the progress of the activity
At the most basic level, SIEM platforms systematically deploy a statistical correlation engine to establish relationships between log entries. Modern SIEMs often include user and entity behavior analytics (UEBA) and security orchestration and automated response (SOAR). SIEM is a platform that can greatly benefit Financial Institutions in the capacity of detecting various forms of cyber-attacks and threats.
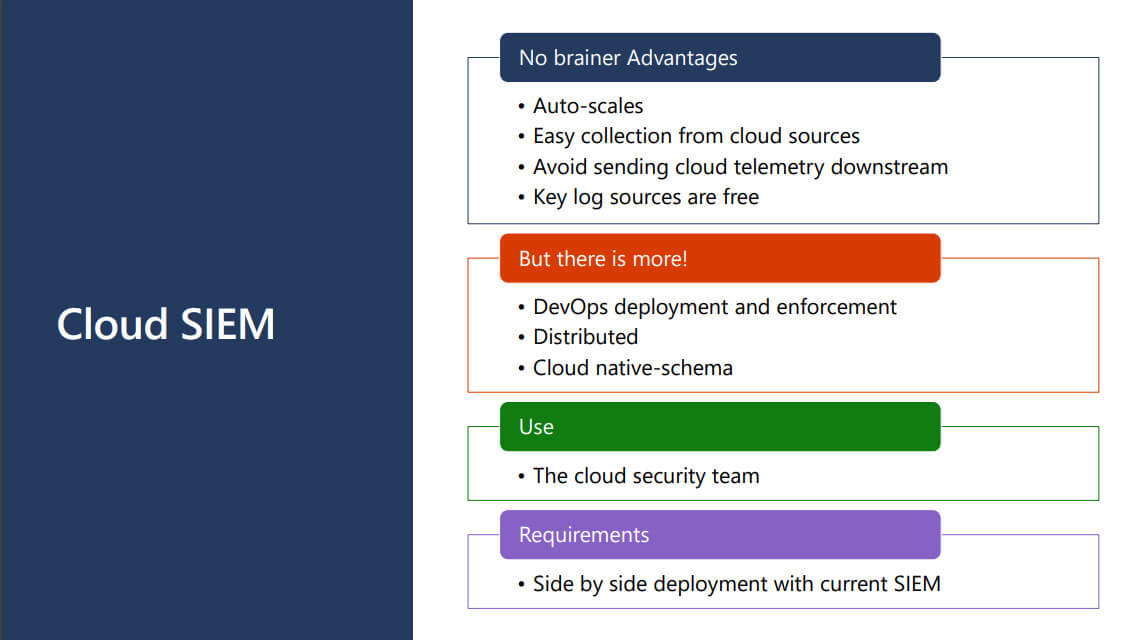
Now what we have a general understanding of Azure Sentinel, let’s look at how enterprises can make the most of Azure Sentinel.
The expanding digital estate
The digital estate of an enterprise is ever expanding with the number of connected devices rising by the minute. This is bringing in a whole lot of challenges for security operations (SecOps) teams like:
- Uninvestigated alerts
- Lack of automation
- Disconnected products
- Unfilled security jobs
- Increasing security data
- Sophistication of threats
- IT deployment and maintenance
SIEM built for on-premises environments struggle to keep pace with new challenges. They are also costly to scale, and its resource heaviness and tools could easily make it an obstacle to enterprise digital transformation. Alert fatigue is at an all-time high, yet few organizations want to spend more money to overcome the problem. Traditional approaches just cannot keep up with the pace of change, and IT departments cannot throw any more money on the problem.
It is this that Microsoft Azure Sentinel, a fully cloud native SIEM, aims to solve. It is designed to serve all four aspects of security operations:
Collect data at cloud scale – across all users, devices, applications, infrastructure – which includes on-premises and multiple clouds.
Detect previously uncovered threats and bring down false positives using analytics and threat detection
Investigate threats with AI and hunt suspicious activities at scale, tapping into old work.
Respond to incidents quickly with built-in orchestration and automation of general tasks.
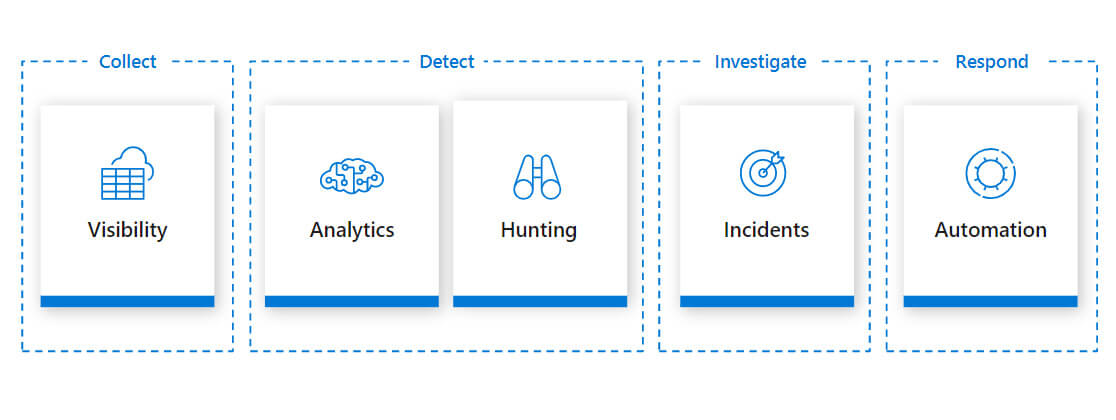
Azure Sentinel eliminates infrastructure and management complexity. It scales readily to meet changing business needs and maximizes team efficiency with intelligent role-based tools. It also lets you have more control over your security operations with insights from Microsoft’s global security operations.
How is Azure Sentinel used?
Sentinel’s use cases
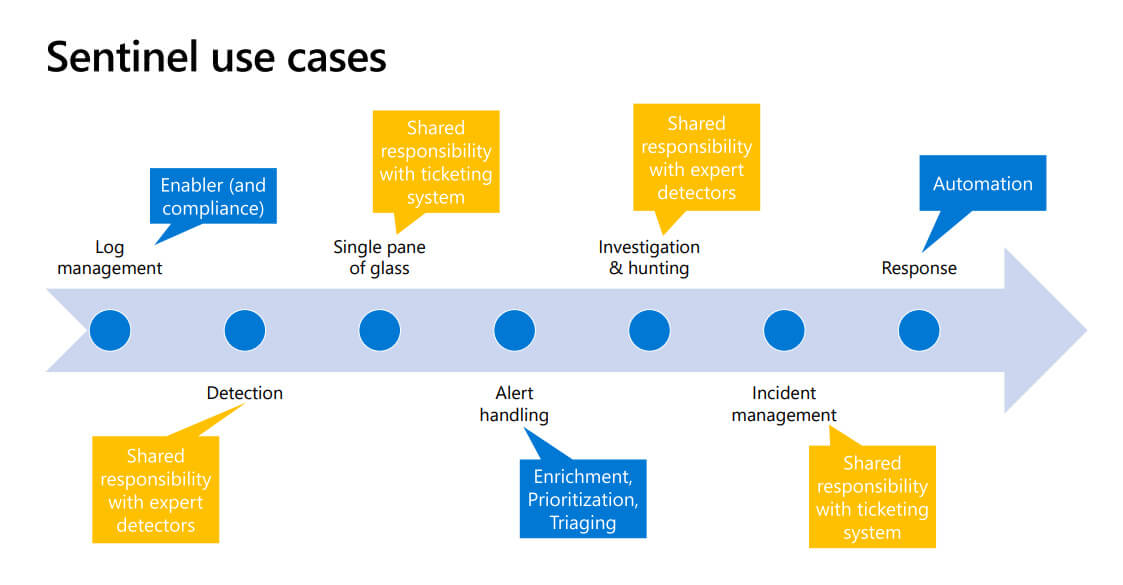
Apart from these use cases, you can also use Azure Sentinel as part of:
1. The MicrosoftSeucitystack, comprising the:
a. The Azure Security Compass: The Azure Security Compass is designed to rapidly increase your Azure security posture. And that lets enterprises, make the right security decisions with best practices, choices and context/recommendations as well as increase users’ familiarity with the Azure Platform Security and Azure Security Center.
b. Using Sentinel, Azure Defender (ASC) and Microsoft Defender (MTP) to detect and respond to aweb shellattack: Microsoft tracks multiple threat actors like ZINC, KRYPTON AND GALLIUM, who have been observed utilizing web shells in their campaigns, usually found using an internet facing server to gain foothold on a victim’s network.
2. The side-by-sideuse cases:
a. Azure Sentinel can be used side-by-side with 3rdparty SIEM tools, leveraging cloud-native SIEM and SOAR capabilities to forward enriched alerts. Splunk is a 3rd party SIEM. Data and notable events can be exported from Splunk to Azure Sentinel using the Azure Sentinel Splunk App.
b. Customers would sometimesprefer to maintain their existing SIEM along with Azure Sentinel, either because they are Azure Sentinel as a cloud SIEM alongside the existing SIEM to monitor on-prem workloads or are using both during the transition period. In this instance, you can send enriched alerts with supporting events from Azure Sentinel to the 3rd party SIEMs.
c.Incident management is one of the main SIEM use cases.For sending an Azure Sentinel Incident into the ServiceNow incident queue, theorganization must create a bi-directional sync of Azure Sentinel with their ITSM tools. When this is done, a security incident created/closed in Azure Sentinel would be created/closed in IT Service Management (ITSM).
d. In Azure,Managed Security Service Providers (MSSP) have an option to protect their intellectual property in an Azure Sentinel environment. IPs could include a Workbook, an analytics rule or a Playbook that extends Sentinel’s functionality.
Cloud architecture; support for multi-workspace and tenants
Azure Sentinel is built atop Log Analytics Workspaces. While you can get the most benefit of Azure Sentinel in a single workspace, in particular use cases, you may have to use multiple workspaces. Some of the common requirements include, multiple Azure tenants, granular data access control, split billing and so on.
In such instances, where there are multiple Azure Sentinel workspaces, mostly across the Azure Active Directory (Azure AD) tenants, there’s a need for central monitoring. To address the need, Azure Sentinel offers multiple workspace capabilities that enable central monitoring, configuration and management, providing a single pane of glass across everything covered by the security operations center (SOC).
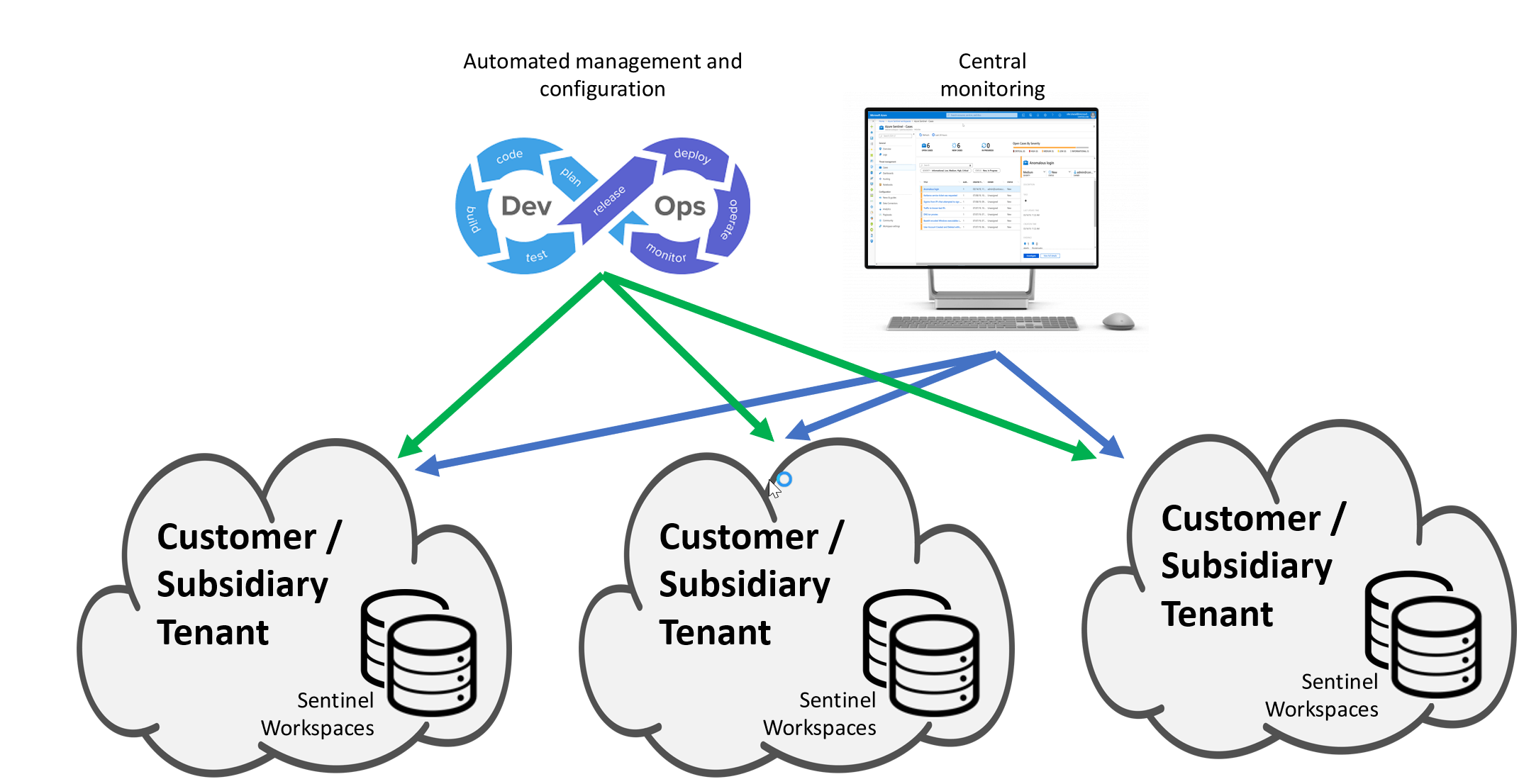
Cross-workspace monitoring capabilities include managing incidents on multiple workspaces, cross workspace querying, scheduled alerts, using cross-workspace workbooks and cross-workspace hunting.
Users can automate the use of Azure Sentinel management API if they’d like to configure and manage multiple Azure Sentinel workspaces.
If you want to manage Azure Sentinel workspace across tenants, you the use the Azure Lighthouse. It allows you the extend your cross-work activities across tenant boundaries, allowing users in the managing tenant to work on Azure Sentinel across all tenants.
Multiple data source connectors to collect events
Azure Sentinel connects with enterprise’ data sources using a number of connectors.
Azure Sentinel comes with several connectors for Microsoft Solutions, available out-of-the-box, that provide real-time integration.
In addition, there are also built-in connectors for broader security system coverage that include non-Microsoft solutions.
And you can also use CEF, Syslog or REST-API protocols for connecting data sources with Azure Sentinel.
Log management and analytics
You can manage and work with Azure Sentinel logs in three different methods:
Storage management: Using Azure Data Explorer or Azure Storage or an event hub for long-term retention. You can also move logs to long-term storage using Logic Apps.
Logs Security: Secure logs by managing access to data using table level RBAC. Using resource RBAC, you can enable multiple teams to use a single workspace. Manage personally identifiable information (PII) from your workspaces. Use LAQueryLogs and AzureActivitiy for auditing Sentinel activities.
Visualization and analysis: You can export your Sentinel data into Excel for performing visual analysis of the data.
Managing threat intelligence
Azure Sentinel uses a form of Cyber Threat Intelligence (CTI) known as threat indicators, more commonly known as Indicators of Compromise (IoCs).
Threat indicators are data that relates URLs, file hashes or IP addresses with known forms for threat activities, such as phishing.
This threat intelligence is often called tactical intelligence because it can be applied to security products and automation in large scale to protect and detect potential threats to an organization.
Creating content on Sentinel
Kusto Query Language
Most Azure Sentinel actions use KQL. A Kusto query is a read-only request to process and return results. The request is stated in plain text, using a data-flow model designed to make the syntax easy to read, author, and automate.
Together with KQL, applying KQL it to Azure Sentinel requires understanding the schema used by Azure Sentinel for key Microsoft, 3rd party sources and most other Azure sources.
Writing the rules
Writing rules requires an understanding of the schema used by Azure Sentinel for key Microsoft, 3rd party sources and most other Azure sources.
Use KQL to write basic filter, correlation, aggregation, behavioral and lookup rules. As well as speed up analysis in Azure Sentinel.
Creating playbooks
Security playbooks are a collection of protocols which are run from Azure Sentinel as response to an alert.
With security playbooks, users can automate responses. The responses can even be run manually or set to run automatically when specific alerts are triggered.
Security playbooks in Azure Sentinel are based on Azure Logic Apps, which means you get the power, flexibility of customization and built-in templates of Logic Apps.
Building your own workbook, reporting and visualization
Azure Workbooks lets you visualize your security threats. While they serve the purpose of dashboards, they go way beyond being a dashboard by being more interactive with the user.
You can use out-of-the–box templates or custom templates and visualize data from your different data sources.
Security Operations on Azure Sentinel
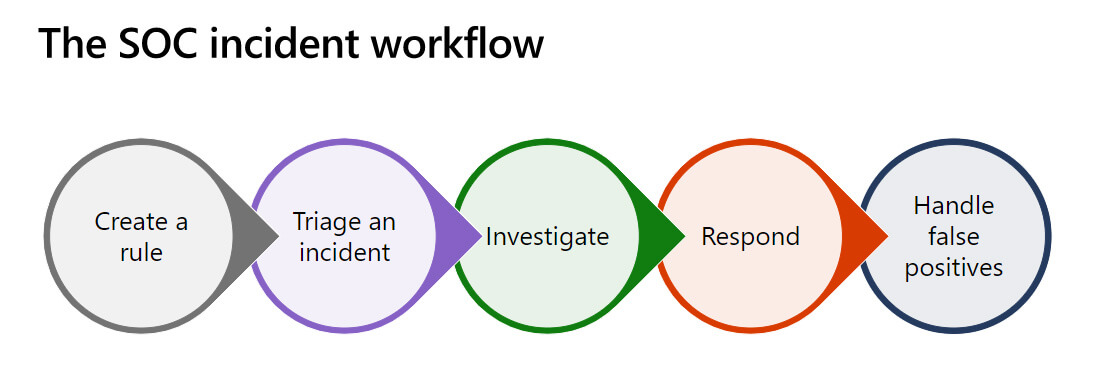
With Azure Sentinel, when you create a rule, you can use built-in analytics, write a rule as well as ensure Service Now integration.
Triaging an incident involves understanding of the incident page, collecting additional data using a playbook, using the investigation graph and updating the status as well as owner
To investigate an incident, you must use a workbook, then go deep to the raw events and collect the evidence need with bookmarks.
For responding to the event, you can first monitor the user using Live Streams. You can then use a playbook to block the user and we can also create a whitelist to resolve false positives.
Threat hunting on Azure Sentinel
Azure Sentinel is a great threat hunting platform. It allows SOC teams to investigate suspicious users, devices, applications.
The tool allows teams to dig deeper into identified anomalies and threat indicators and look for evidence of attack.
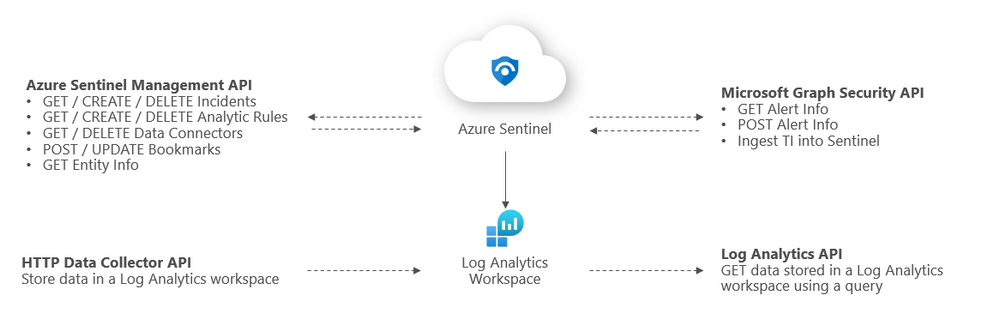
Extending the possibilities of Azure Sentinel with APIs
There are several different APIs that you can interact with. We can categorize Azure Sentinel APIs as follows:
- Azure Sentinel Management API
- Microsoft Graph Security API
- Log Analytics API
- HTTP Data Collector API
Conclusion
The above article only serves as a quick introduction to setting up and building your security operations framework on Azure Sentinel. For a more detailed training, visit Become an Azure Sentinel Ninja: The complete level 400 training – Microsoft Tech Community.
